Byte25 is a complete solution providing scalable IT visibility and security monitoring for organisations ranging from SME’s through to large enterprise. The Byte25 solution delivers deep insight into network performance and cyber security incidents to help you regain control of your network ensuring consistent user experience and security.
Byte25 understands the importance of resolving network and security issues fast. You need more intuitive, lower cost solutions that require less effort to get to the root cause of problems. As more technologies, like SD-WAN and multi-cloud services, are thrown at your business – you increasingly need wide visibility of all every piece of traffic traversing the network.
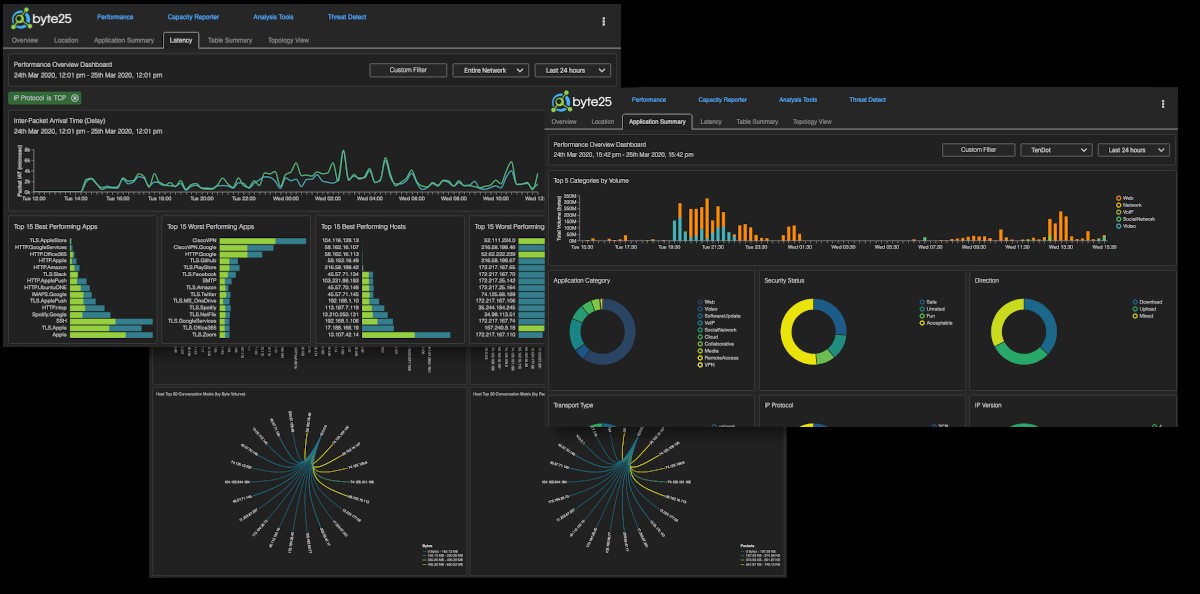
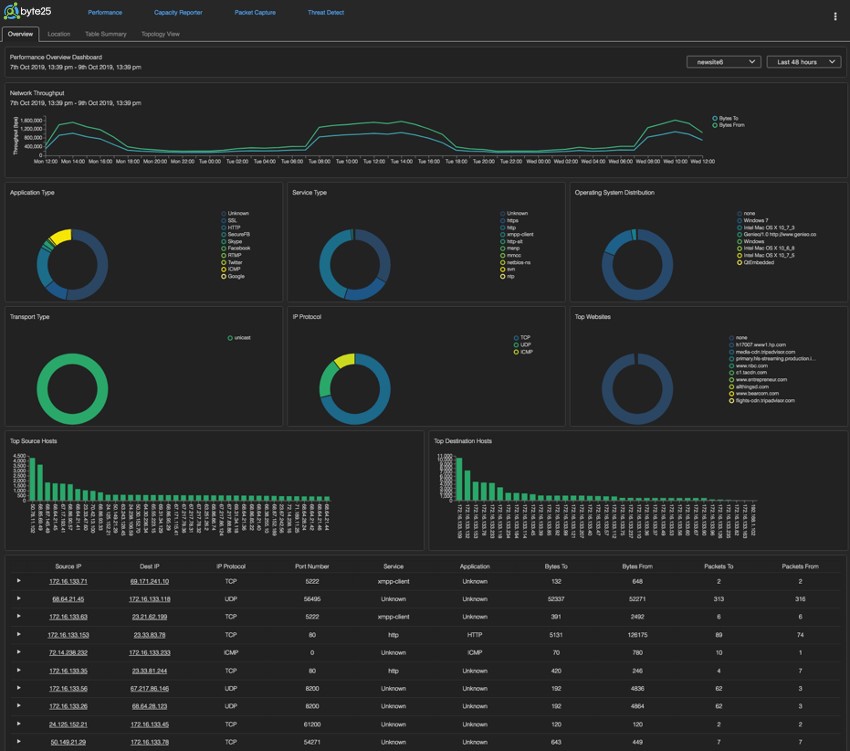
Byte25 delivers a comprehensive set of reports from the central web based dashboard (either cloud based or on-premise). The central dashboard correlates data from all installed appliances to provide a clear picture of network performance and cyber security posture from a very high level right down to each individual flow. IT visibility shouldn’t be hard, Byte25 provides the perfect solution to plug the visibility black spots.
Visibility tools shouldn’t be complex. Ease of use is essential in ensuring that tools continue to deliver return on investment after deployment. The Byte25 engineering team has been building visibility tools for decades and have a deep understanding of how to present information in a simple intuitive way. The Byte25 performance dashboard provides a quick and detailed summary of site and network performance with context sensitive 'clickable' graphs providing the ability to drill down from a high level view to specific data in a few simple clicks.
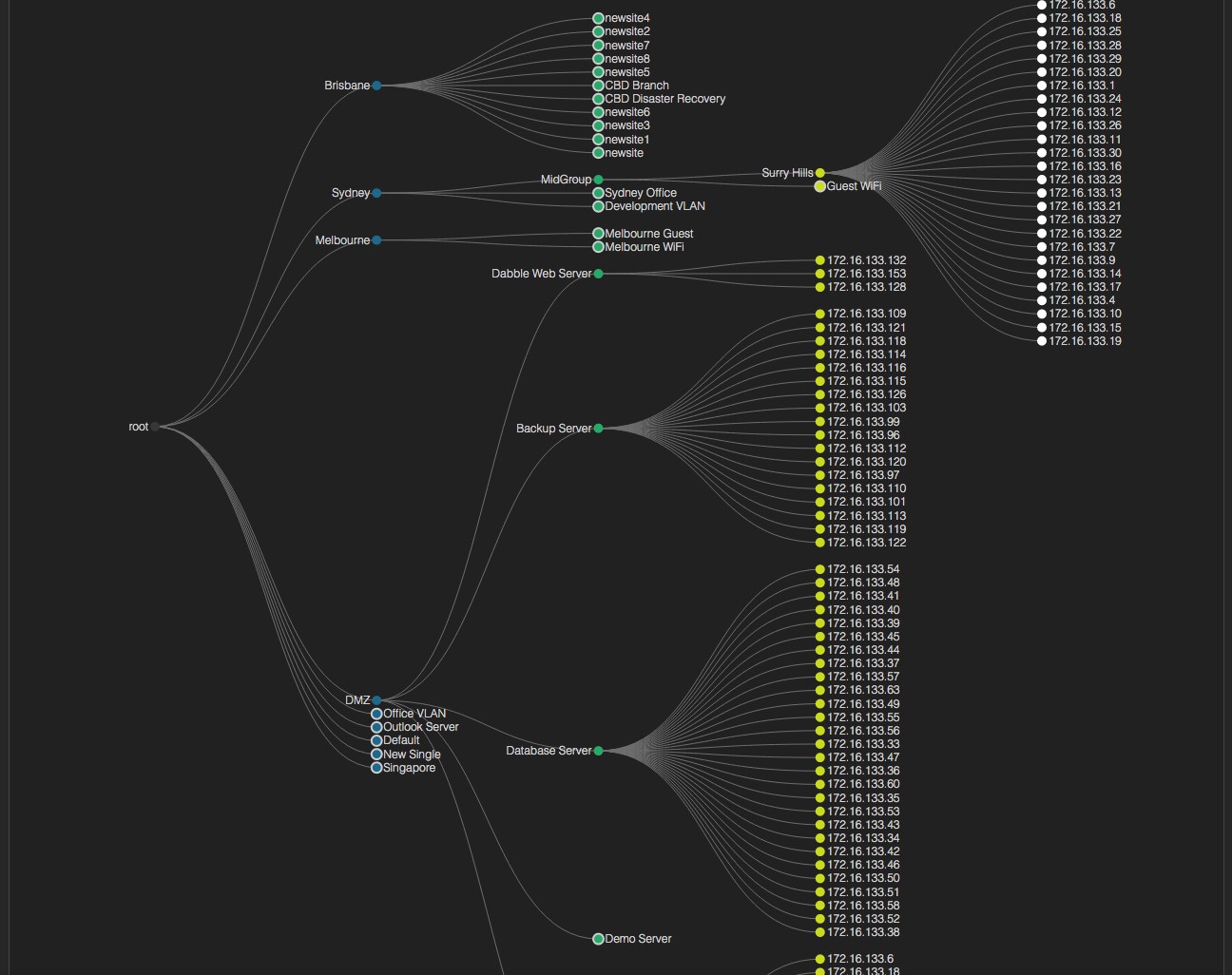
Remote sites typically consist of multiple subnets or VLANs. Byte25 monitors multiple subnets within each branch and provides a a tabular view to allow for quick identification of subnet specific performance or potential issues. The subnet view presents summary information as well as hyperlinks links to easily drill down for more information.
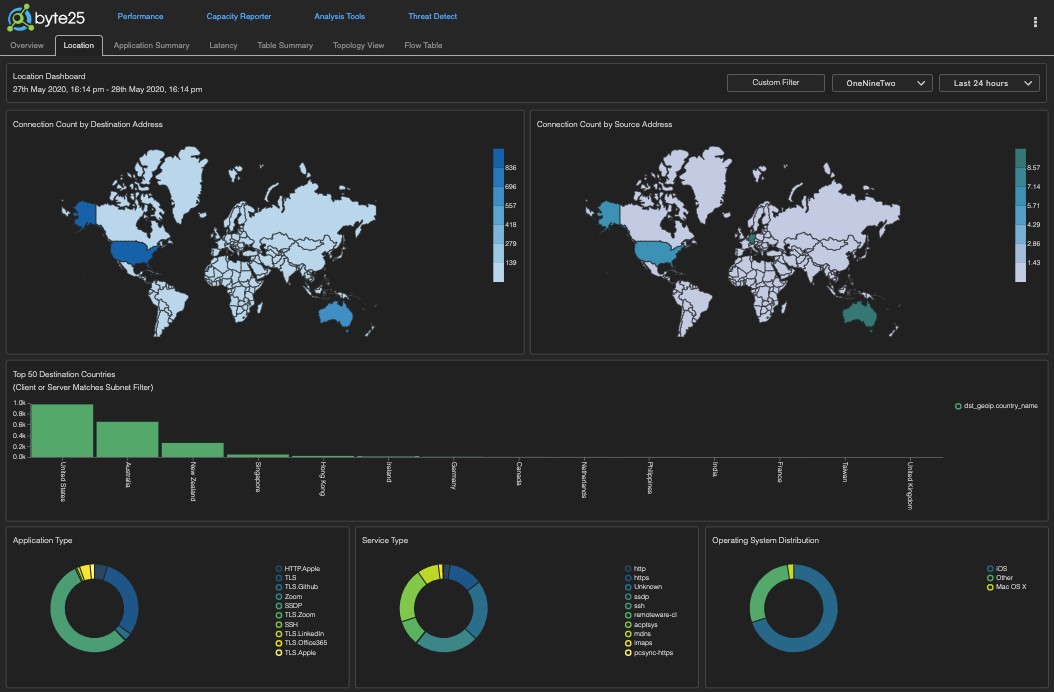
Modern business work flows require significant user interaction with Internet facing applications and cloud based services. Byte25 identifies the geographic location of all publicly facing traffic flows to easily identify where users are travelling to, on the net. By monitoring the source country of incoming traffic, anomalous or potentially malicious traffic can often be identified.
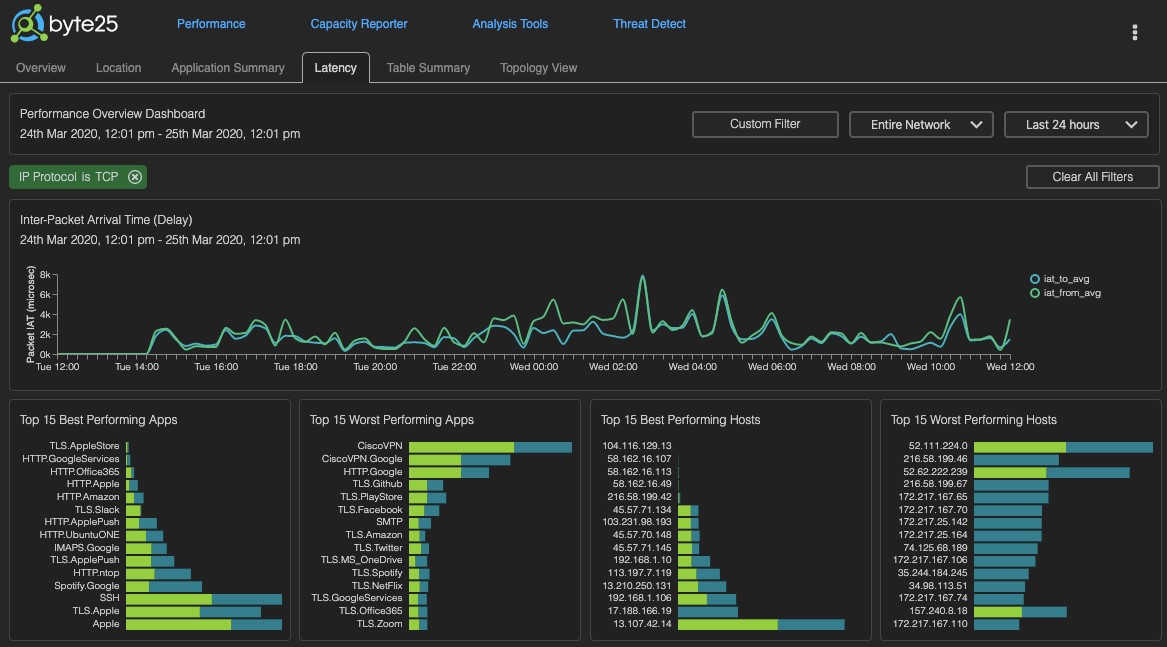
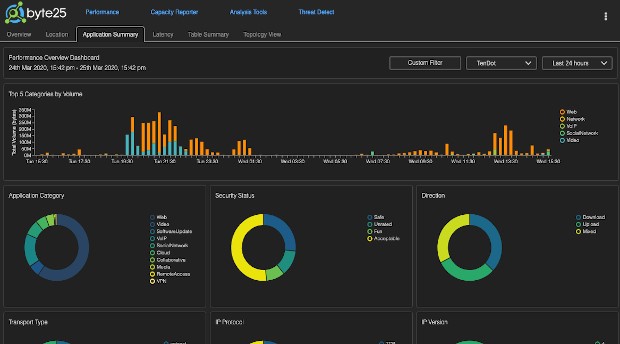
Byte25 utilises deep packet inspection (DPI) techniques to inspect packet payloads to identify specific applications traversing the network. DPI techniques allow for comprehensive application classification even where applications may share common TCP port numbers such as HTTP. As the volume of encrypted traffic increases, DPI becomes increasingly challenging. Byte25 addresses this challenge by utilising industry leading techniques such a TLS inspection to ensure effective application classification for encrypted and non-encrypted traffic.
Threat Detection at the edge is becoming increasingly relevant as more remote and branch sites connect directly to the internet via SD-WAN style connections. Even where networks are secured with effective perimeter security measures such as firewalls, internal threat detection provided by Byte25 can often identify malicious lateral movement behind the firewall. Correlation of the Threat Detection and Performance datasets within the Byte25 solution provides the most comprehensive visibility solution for identifying and acting upon anomalous network activity.
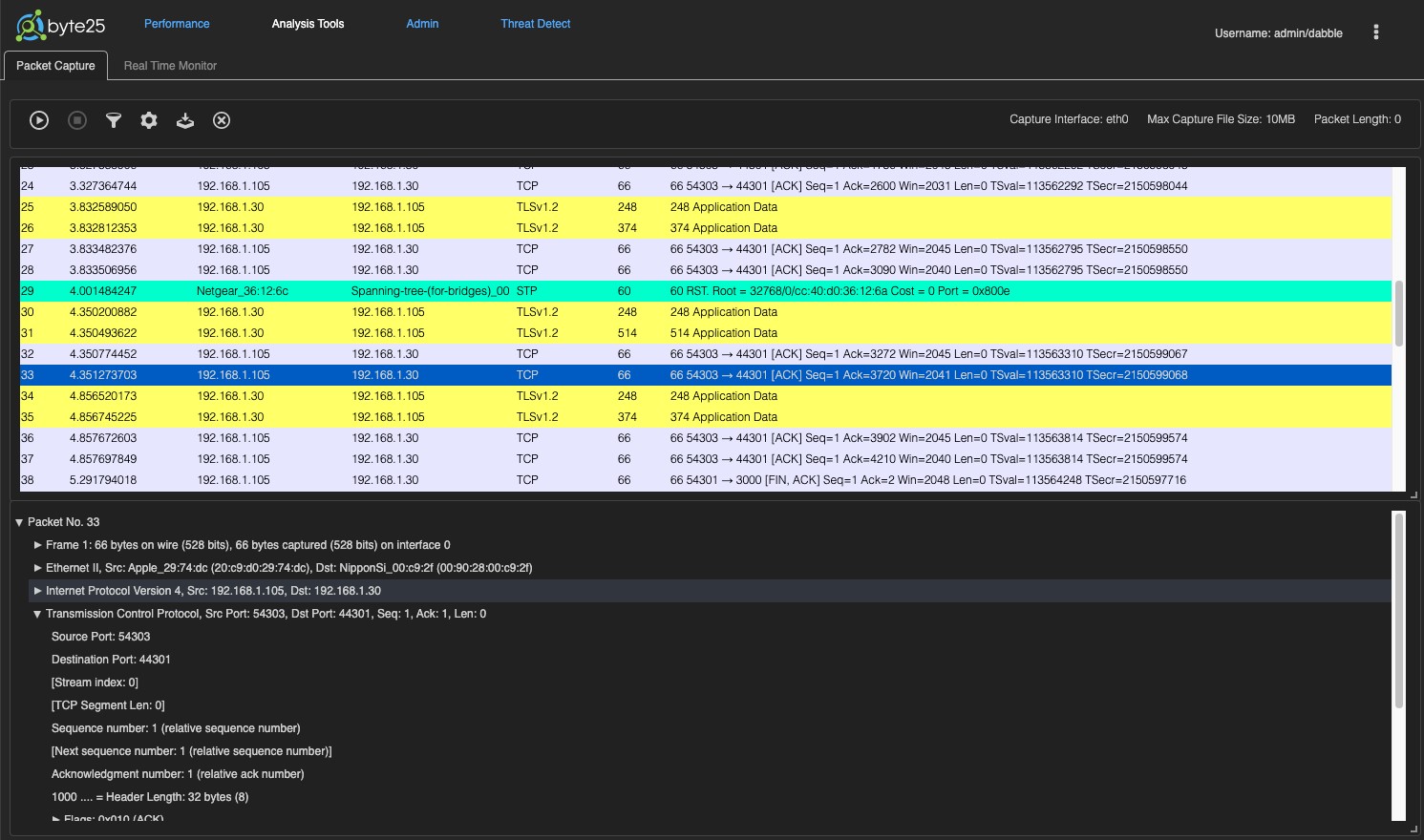
A full packet capture engine is included with a Wireshark style web front end including full filtering capability. The packet capture module allows for network engineers to perform full packet capture and decodes at remote sites using a normal web browser. This ability negates the requirement to dispatch an engineer with a dedicated packet analyser. Packet captures are stored in standard PCAP format and may be downloaded for further analysis in third party analysers if required.
In addition to standard network metrics collection, Byte25 has a real time analysis and troubleshooting tool called the Real Time Monitor. The Real Time Monitor allows network engineers to run ad hoc report in real time with as little as 1 second granularity. The real time monitor supports a wide range of network metrics critical for identification of network issues including latency, throughput, congestion, packet loss ,as well as application level metrics to specific appliactions such as VoIP.
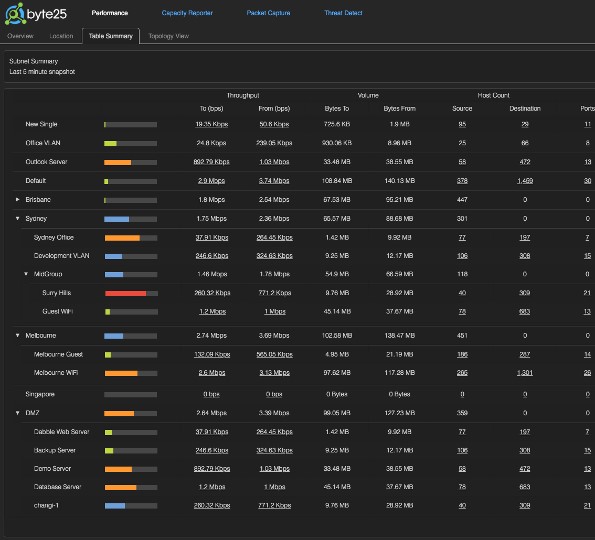
Whilst Byte25 appliances can operate standalone, they are commonly coupled with a broader distributed solution for complete enterprise visibility. Byte25 can export information to a cenralised cloud or on-prem server to provide a single data repository for enterprise wide visibility. The Byte25 distributed scaleable architecture allows for visibility from very small sites right through to large enterprise potentially monitoring thousands of subnets.
...